Davical on NetBSD
Didn’t found any davical tutorial for NetBSD, here’s mine, hope this will be useful to someone. At the time of this writing, it’s based on NetBSD 10RC1 that just came out.
Postgresql database
pkgin install postgresql14
cp /usr/pkg/share/examples/rc.d/pgsql /etc/rc.d
/etc/rc.d/pgsql oneinitdb -E unicode
echo "pgsql=YES" >> /etc/rc.conf
Add necessary permission for Davical in /usr/pkg/pgsql/data/pg_hba.conf and start Postgresql:
--- pg_hba.conf.ori 2023-11-23 09:51:12.499873121 +0000
+++ pg_hba.conf 2023-11-23 09:56:30.759686301 +0000
@@ -87,6 +87,8 @@
# "local" is for Unix domain socket connections only
local all all trust
+local davical davical_app trust
+local davical davical_dba trust
# IPv4 local connections:
host all all 127.0.0.1/32 trust
# IPv6 local connections:
/etc/rc.d/pgsql start
Apache
Did choose Apache as this is the web server that work out of the box (well kind of) with Davical but some others can be used (Lighthttpd, NGINX, etc).
Installation
It’s important have Apache installed before Davical (and not the other way around), this should be specific to NetBSD specific.
pkgin install apache-2.4 ap24-php81
cp /usr/pkg/share/examples/rc.d/apache /etc/rc.d
echo "apache=YES" >> /etc/rc.conf
TLS certificates
Create (make sure that CN will match server FQDN):
cp /usr/share/examples/openssl/openssl.cnf /etc/openssl/
cd /usr/pkg/etc/httpd
openssl genrsa -out server.key 4096
chmod 400 server.key
openssl req -new -key server.key -out server.csr
Self-sign it:
openssl x509 -sha256 -req -days 365 \
-in server.csr \
-signkey server.key \
-out server.crt
Setup
cd /usr/pkg/etc/httpd
httpd.conf
--- httpd.conf.ori 2023-11-23 10:47:23.776577882 +0000
+++ httpd.conf 2023-11-23 10:53:57.117542382 +0000
@@ -63,8 +63,8 @@
# Example:
# LoadModule foo_module modules/mod_foo.so
#
-LoadModule mpm_event_module lib/httpd/mod_mpm_event.so
-#LoadModule mpm_prefork_module lib/httpd/mod_mpm_prefork.so
+#LoadModule mpm_event_module lib/httpd/mod_mpm_event.so
+LoadModule mpm_prefork_module lib/httpd/mod_mpm_prefork.so
#LoadModule mpm_worker_module lib/httpd/mod_mpm_worker.so
LoadModule authn_file_module lib/httpd/mod_authn_file.so
#LoadModule authn_dbm_module lib/httpd/mod_authn_dbm.so
@@ -88,7 +88,7 @@
#LoadModule cache_module lib/httpd/mod_cache.so
#LoadModule cache_disk_module lib/httpd/mod_cache_disk.so
#LoadModule cache_socache_module lib/httpd/mod_cache_socache.so
-#LoadModule socache_shmcb_module lib/httpd/mod_socache_shmcb.so
+LoadModule socache_shmcb_module lib/httpd/mod_socache_shmcb.so
#LoadModule socache_dbm_module lib/httpd/mod_socache_dbm.so
#LoadModule socache_memcache_module lib/httpd/mod_socache_memcache.so
#LoadModule socache_redis_module lib/httpd/mod_socache_redis.so
@@ -145,7 +145,7 @@
#LoadModule session_dbd_module lib/httpd/mod_session_dbd.so
#LoadModule slotmem_shm_module lib/httpd/mod_slotmem_shm.so
#LoadModule slotmem_plain_module lib/httpd/mod_slotmem_plain.so
-#LoadModule ssl_module lib/httpd/mod_ssl.so
+LoadModule ssl_module lib/httpd/mod_ssl.so
#LoadModule dialup_module lib/httpd/mod_dialup.so
#LoadModule http2_module lib/httpd/mod_http2.so
#LoadModule lbmethod_byrequests_module lib/httpd/mod_lbmethod_byrequests.so
@@ -170,7 +170,8 @@
#LoadModule speling_module lib/httpd/mod_speling.so
#LoadModule userdir_module lib/httpd/mod_userdir.so
LoadModule alias_module lib/httpd/mod_alias.so
-#LoadModule rewrite_module lib/httpd/mod_rewrite.so
+LoadModule rewrite_module lib/httpd/mod_rewrite.so
+LoadModule php_module /usr/pkg/lib/httpd/mod_php8.so
<IfModule unixd_module>
#
@@ -270,7 +271,7 @@
# is requested.
#
<IfModule dir_module>
- DirectoryIndex index.html
+ DirectoryIndex index.html index.php
</IfModule>
#
@@ -409,6 +410,9 @@
AddType application/x-compress .Z
AddType application/x-gzip .gz .tgz
+ #php
+ AddType application/x-httpd-php .php
+
#
# AddHandler allows you to map certain file extensions to "handlers":
# actions unrelated to filetype. These can be either built into the server
@@ -506,13 +510,16 @@
# Various default settings
#Include etc/httpd/httpd-default.conf
+#davical
+Include /usr/pkg/etc/davical/davical-ssl.conf
+
# Configure mod_proxy_html to understand HTML4/XHTML1
<IfModule proxy_html_module>
Include etc/httpd/proxy-html.conf
</IfModule>
# Secure (SSL/TLS) connections
-#Include etc/httpd/httpd-ssl.conf
+Include etc/httpd/httpd-ssl.conf
#
# Note: The following must must be present to support
# starting without SSL on platforms with no /dev/random equivalent
httpd-ssl.conf
--- httpd-ssl.conf.ori 2023-11-23 10:48:03.316390936 +0000
+++ httpd-ssl.conf 2023-11-23 11:12:20.650561708 +0000
@@ -49,8 +49,8 @@
# ensure these follow appropriate best practices for this deployment.
# httpd 2.2.30, 2.4.13 and later force-disable aNULL, eNULL and EXP ciphers,
# while OpenSSL disabled these by default in 0.9.8zf/1.0.0r/1.0.1m/1.0.2a.
-SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
-SSLProxyCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
--- httpd-ssl.conf.ori 2023-11-23 10:48:03.316390936 +0000
+++ httpd-ssl.conf 2023-11-23 11:12:20.650561708 +0000
@@ -49,8 +49,8 @@
# ensure these follow appropriate best practices for this deployment.
# httpd 2.2.30, 2.4.13 and later force-disable aNULL, eNULL and EXP ciphers,
# while OpenSSL disabled these by default in 0.9.8zf/1.0.0r/1.0.1m/1.0.2a.
-SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
--- httpd-ssl.conf.ori 2023-11-23 10:48:03.316390936 +0000
+++ httpd-ssl.conf 2023-11-23 11:12:20.650561708 +0000
@@ -49,8 +49,8 @@
# ensure these follow appropriate best practices for this deployment.
# httpd 2.2.30, 2.4.13 and later force-disable aNULL, eNULL and EXP ciphers,
# while OpenSSL disabled these by default in 0.9.8zf/1.0.0r/1.0.1m/1.0.2a.
-SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
+#SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
--- httpd-ssl.conf.ori 2023-11-23 10:48:03.316390936 +0000
+++ httpd-ssl.conf 2023-11-23 11:12:20.650561708 +0000
@@ -49,8 +49,8 @@
# ensure these follow appropriate best practices for this deployment.
# httpd 2.2.30, 2.4.13 and later force-disable aNULL, eNULL and EXP ciphers,
# while OpenSSL disabled these by default in 0.9.8zf/1.0.0r/1.0.1m/1.0.2a.
-SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
-SSLProxyCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
+#SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
+#SSLProxyCipherSuite HIGH:MEDIUM:!MD5:!RC4:!3DES
# By the end of 2016, only TLSv1.2 ciphers should remain in use.
# Older ciphers should be disallowed as soon as possible, while the
@@ -62,8 +62,8 @@
# those protocols which do not support forward secrecy, replace
# the SSLCipherSuite and SSLProxyCipherSuite directives above with
# the following two directives, as soon as practical.
-# SSLCipherSuite HIGH:MEDIUM:!SSLv3:!kRSA
-# SSLProxyCipherSuite HIGH:MEDIUM:!SSLv3:!kRSA
+SSLCipherSuite HIGH:MEDIUM:!SSLv3:!kRSA
+SSLProxyCipherSuite HIGH:MEDIUM:!SSLv3:!kRSA
# User agents such as web browsers are not configured for the user's
# own preference of either security or performance, therefore this
@@ -118,18 +118,18 @@
## SSL Virtual Host Context
##
-<VirtualHost _default_:443>
+#<VirtualHost _default_:443>
# General setup for the virtual host
-DocumentRoot "/usr/pkg/share/httpd/htdocs"
-ServerName www.example.com:443
-ServerAdmin you@example.com
-ErrorLog "/var/log/httpd/error_log"
-TransferLog "/var/log/httpd/access_log"
+#DocumentRoot "/usr/pkg/share/httpd/htdocs"
+#ServerName www.example.com:443
+#ServerAdmin you@example.com
+#ErrorLog "/var/log/httpd/error_log"
+#TransferLog "/var/log/httpd/access_log"
# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
-SSLEngine on
+#SSLEngine on
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
@@ -287,4 +287,4 @@
CustomLog "/var/log/httpd/ssl_request_log" \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
-</VirtualHost>
+#</VirtualHost>
Davical
Package installation
pkgin install php81-davical-1.1
Database creation
This script will initialise the DB
sudo -u pgsql /usr/pkg/share/davical/dba/create-database.sh
Note the admin account password:
Supported locales updated.
Updated view: dav_principal.sql applied.
CalDAV functions updated.
RRULE functions updated.
Database permissions updated.
NOTE
====
The password for the 'admin' user has been set to 'blablobli'
Thanks for trying DAViCal! Check the configuration in /usr/pkg/etc/davical/config.php.
For help, look at our website and wiki, or visit #davical on irc.oftc.net.
Virtual Host
I choose a vhost setup with tls support:
vi /usr/pkg/etc/davical/davical-ssl.conf
# DAViCal Calendar Server
<VirtualHost _default_:443>
ServerName cal.home.internal
DocumentRoot /usr/pkg/share/davical/htdocs
DirectoryIndex index.php index.html
ServerName cal.home.internal
Alias /images/ /usr/pkg/share/davical/htdocs/images/
<Directory /usr/pkg/share/davical/htdocs>
DirectoryIndex index.php index.html
AllowOverride None
# for Apache from 2.4 use
Require all granted
# for Apache before 2.4 use
#Order allow,deny
#Allow from all
# These are usually not necessary (set correctly by default)
#AcceptPathInfo On
#php_value include_path /usr/share/php/awl/inc
#php_value magic_quotes_gpc 0
#php_value register_globals 0
#php_value error_reporting "E_ALL & ~E_NOTICE"
#php_value default_charset "utf-8"
# Some people want this. YMMV.
#php_admin_value open_basedir /usr/share/awl/inc/:/usr/share/davical/:/etc/davical/
</Directory>
RewriteEngine On
# Redirect /.well-known URLs
RewriteRule ^/\.well-known/(.*)$ /caldav.php/.well-known/$1 [NC,L]
# Optionally: redirect /principals/users/ as well
RewriteRule ^/principals/users/(.*)$ /caldav.php/$1 [NC,L]
# Optionally: Put DAViCal in the root
# NOTE: this will break other applications that rely on mod_rewrite!
#
# Not if it's the root URL. You might want to comment this out if you
# want to use an explicit /index.php for getting to the admin pages.
#RewriteCond %{REQUEST_URI} !^/$
#RewriteCond %{REQUEST_URI} !^/davical/$
#
# Not if it explicitly specifies a .php program, html page, stylesheet or image
#RewriteCond %{REQUEST_URI} !\.(php|html|css|js|png|gif|jpg|ico)
#
# Everything else gets rewritten to /caldav.php/...
#RewriteRule ^(.*)$ /caldav.php$1 [NC,L]
SSLEngine on
SSLCertificateFile "/usr/pkg/etc/httpd/server.crt"
#ErrorLog ${APACHE_LOG_DIR}/error_davical.log
#LogLevel alert
#CustomLog ${APACHE_LOG_DIR}/access_davical.log combined
</VirtualHost>
First run
The websever can now be started:
service apache start
Davical admin page can now be reached trough https://server.fqdn (you will have to trust the self-signed certificate in your browser)
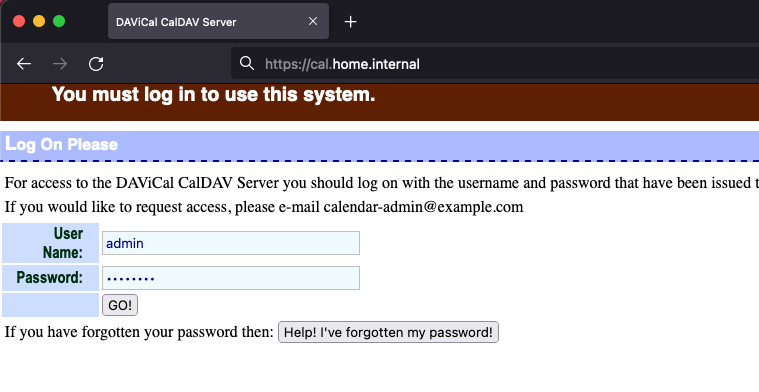
You can now login with the admin account using the password from the Database creation step and create user(s):
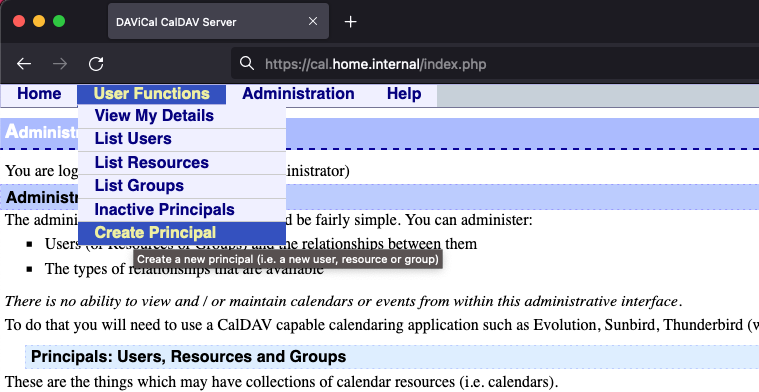
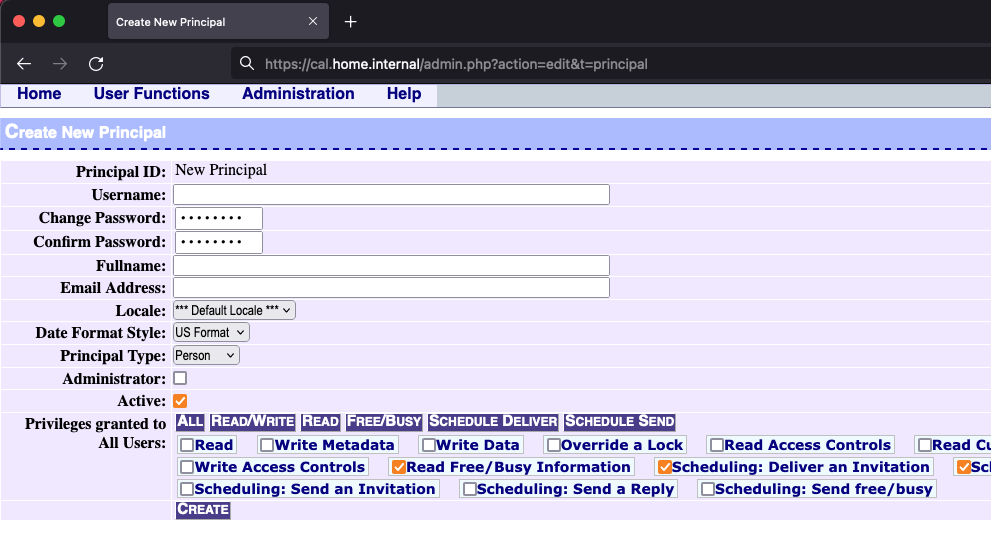
Client configuration
This setup should work with most CalDAV / CardDAV client (DAVx5, IOS, etc) see Davical documentation for detailed instructions.